Phishing is a common form of cybercrime. However, despite all the information we have about scam email, people still fall for it.
Action Fraud has received more than 400,000 reports of Phishing Emails each year. According to the Mimecast’s State of Email Security 2020 report, 58% of organizations saw an increase in phishing attacks over the past 12 month.
Verizon’s most recent Data Breach Investigations Report revealed that more than half of data breaches were social engineering attacks like phishing.
This blog uses real examples of phishing emails to show five clues that will help you identify scams.
1. The message is sent from a public email domain
An address ending in ‘@gmail.com will not be used by legitimate organizations to send email.
Not even Google.
Except for small businesses, most organization’s will have their own email domains and company accounts. Google’s legitimate email addresses will include the following: “@google.com”
The message is likely to be legitimate if the domain name (the bit following the @ symbol), matches the sender.
You can check the domain name of an organization by entering its name into a search engine.
It is easy to detect phishing, but cybercriminals have many tricks up their sleeves.
Tip: Pay attention to the email address and not just the sender
Many people don’t look at an email address from which a message was sent.
Your inbox has a name like “IT Governance” and a subject line. You already know or think you know who the email is from when you open it. Then you can jump right into the content.
Crooks often choose to display their fake email addresses with a display name. This doesn’t necessarily have to be related to the email address.
They can use a fake email address which will be displayed in your inbox under the name Google.
Criminals don’t rely on ignorance to commit crimes. They will put the name of the fake organisation in the local address.
Here’s an example of phishing emails that mimic PayPal.

This email is almost flawless. The message uses PayPal’s logo as the header. It is professionally designed and makes the request seem plausible.
But as much as it attempts to replicate a genuine email from PayPal, there’s one huge red flag: the sender’s address is ‘paypal@notice-access-273.com’.
An authentic email from PayPal should have the name of the organization in the domain name. This indicates that the email came from (@) PayPal. This is evidence that the scam is working.
Sometimes, just including PayPal in a message is enough to fool people.
They may be satisfied with the PayPal word in their email address, or they might not know the difference between the local and domain names.
2. The domain name is misspelt
Another clue is hidden in domain names. This clue provides a strong indicator of phishing scams. Unfortunately, it complicates our previous clue.
Problem is, anyone can purchase a domain name through a registrar. Even though every domain name must be unique there are many ways to create addresses that can’t be distinguished from the one being spoofed.
In the episode What Kind of Idiot Gets Phished?, Gimlet Media’s podcast “Reply All” demonstrated just how difficult it is to identify a fake domain. Phia Bennin (the show’s producer) hired an ethical hacker in order to phish different employees.
The hacker purchased the domain gimletrnedia.com (rather than m-ed-ia) and assumed Bennin’s identity.
His con was so successful, he duped the hosts of Gimlet Media’s CEO & president.
Help criminal hackers Doesn’t mean you have to be a victim
Bennin explained that you don’t have to be hacked by criminals to get vital information.
Daniel Boteanu, an ethical hacker, was able to see the time the link was clicked and, in one case, that the link had been opened on multiple devices.
He reasoned that although the target was curious, he kept returning to the link. However, he was suspicious enough to not follow the instructions.
Boteanu explains:
I’m guessing [the target] saw that something was going on and he started digging a bit deeper and […] trying to find out what happened […]
And I’m suspecting that after, [the target] maybe sent an email internally saying, “Hey guys! This is what I got. Just be careful. Don’t click on this […] email.
Boteanu’s theory is exactly what had happened. But why does that help the hacker? Bennin elaborates:
The reason Daniel had thought [the target] had done that is because he had sent the same email to a bunch of members of the team, and after [the target] looked at it for the fourth time, nobody else clicked on it.
And that’s okay for Daniel because he can try, like, all different methods of phishing the team, and he can try it a bunch of different times. [And] since [the target is] sounding alarm bells, he probably won’t include [him] in the next phishing attempt.
In many ways, criminal hackers can still win, even if they succeed in their first attempt.
This means that indecisiveness when detecting a phishing scheme gives clues to the scammer as to where your organization’s strengths and weaknesses are.
They can launch other scams using this information with minimal effort, and they can continue doing so until someone falls for their trap.
Criminal hackers can only make one mistake per employee to succeed. Therefore, every employee in your organization must have confidence in their ability detect a scam immediately.
3. It is poorly written
Poor spelling and grammar are often indicators that an email scam.
Many will tell you that these errors are part a “filtering system” in which cybercriminals target only the most stupid.
It is believed that if someone doesn’t pay attention to the message’s format, they are less likely to be able to detect clues in the scammer’s scheme.
This does not apply to outrageous schemes such as the Nigerian prince scam. You have to be extremely naïve in order to fall for these.
This scam and others like it are all manually operated. Once someone accepts the bait, the scammer must reply. It is a benefit to the scammers to ensure that the pool of respondents only includes those who may believe the rest.
This doesn’t mean that phishing is illegal.
Automated Attacks
Phishers don’t have to monitor email inboxes or send targeted responses. They just send thousands of carefully crafted messages to unsuspecting victims.
Therefore, it’s not necessary to filter potential respondents. This reduces the number of potential victims, and allows those who weren’t harmed to alert others about the scam.
Why is it that so many phishing email are poorly written? The obvious reason is that scammers don’t know how to write.
Many of these people are not native English speakers and come from backgrounds that make it difficult or impossible to learn English.
This will make it easier to distinguish between a genuine sender’s typo and a scam.
Top tip – Look out for spelling and grammar mistakes
Scammers often use a translation machine or spellchecker to create phishing messages. This will not always give them the correct context but will provide all the words they need.
This is an example of a scam that imitates Windows.

Although no word is misspelled, the message contains grammatical errors that would be obvious to a native speaker. For example, “We detected something unusual enough to use an app”.
There are also many misspelled words like “a malicious user might try to access” or “Please contact Security Communication Center”.
These mistakes are similar to the ones people make when learning English. This is almost certain to be a fraud.
However, this does not mean that any email with a typo in it is a fraud. Everybody makes mistakes from time to time, especially if they are in a rush.
The recipient must therefore examine the context and decide if it is a sign of something more sinister. Asking:
- It could be a sign of a typo, such as hitting an adjacent key.
- Are you unsure if it is a mistake that a native speaker should not make (grammar incoherence, words in the wrong context)
- Is this an email template that should have been written and copied?
- Are you able to compare it with other messages I have received from the person?
If in doubt, you can look for additional clues or contact the sender via another method of communication. This could be in person, via phone, through their website, or via an instant messaging client.
4. It contains suspicious attachments and links
Phishing emails can come in many forms. Although we’ve been focusing on email scams, you may also receive scam texts, phone calls, or posts on social media.
No matter how many phishing emails you receive, all of them contain a payload. It could be either an infected attachment you are asked to download, or a link to a fake website.
These payloads are used to collect sensitive information such as login credentials and credit card details.
What’s an infected attachment?
Infected attachments are documents that appear to be harmless but contain malware. A typical example is the one below. The phisher claims that he is sending an invoice.

It doesn’t really matter if the recipient expects to be invoiced by this person. Most recipients won’t know what the attachment is until they open it.
They’ll find that the invoice was not intended for them when they open the attachment. But it’s too late. The malware in the document could execute any number of malicious activities .
If you are not sure that an attachment is legitimate, we recommend that you do not open it. You should still be suspicious of any attachments.
If you get a pop-up warning that the file is not legitimate or the application asks for you to change your settings, don’t go ahead.
You can contact the sender via an alternative method of communication to confirm that it is legitimate.
Suspicious links
If the destination address is not in the same context as the rest of the email, it’s easy to spot a suspicious hyperlink.
If you get an email from Netflix, for example, the link should direct you to an address that starts with ‘netflix.com.
Many scam and legitimate emails conceal the destination address in a button so that it is not immediately obvious where the link takes you.

This example shows that you would know if something was suspicious if the email contained the destination address.
The rest of the message is convincing and you may click the link without thinking twice.
You can prevent yourself from falling for such schemes by learning how to verify links before you open them.
This is easy: hover your mouse over the link on a computer and the destination address will appear in a small bar at the bottom of the browser.
Hold down the link on a mobile device and a popup window will open containing the link.
5. The message creates a sense of urgency
Scammers know that many of us procrastinate. We get an email with important information and decide to deal with it later.
The more you think about something, however, the more likely it is that you will notice things that aren’t right.
Perhaps you discover that the company doesn’t reach you at that email address or that a colleague didn’t send you any documents.
Even if you don’t get the ‘aha’ moment, a new set of eyes could help reveal the true nature of the message.
Many scams ask you to act quickly or it will be too late. This is evident in all of the examples we have seen.
PayPal, Windows, and Netflix offer services that are frequently used. Any problems with these accounts can cause immediate inconveniences.
Your business is dependent on you
Scams at work can also use a manufactured sense of urgency.
Criminals know we are likely to give up everything if our boss sends us a crucial request. This is especially true if other senior colleagues have supposedly been waiting for us.
This is a typical example:
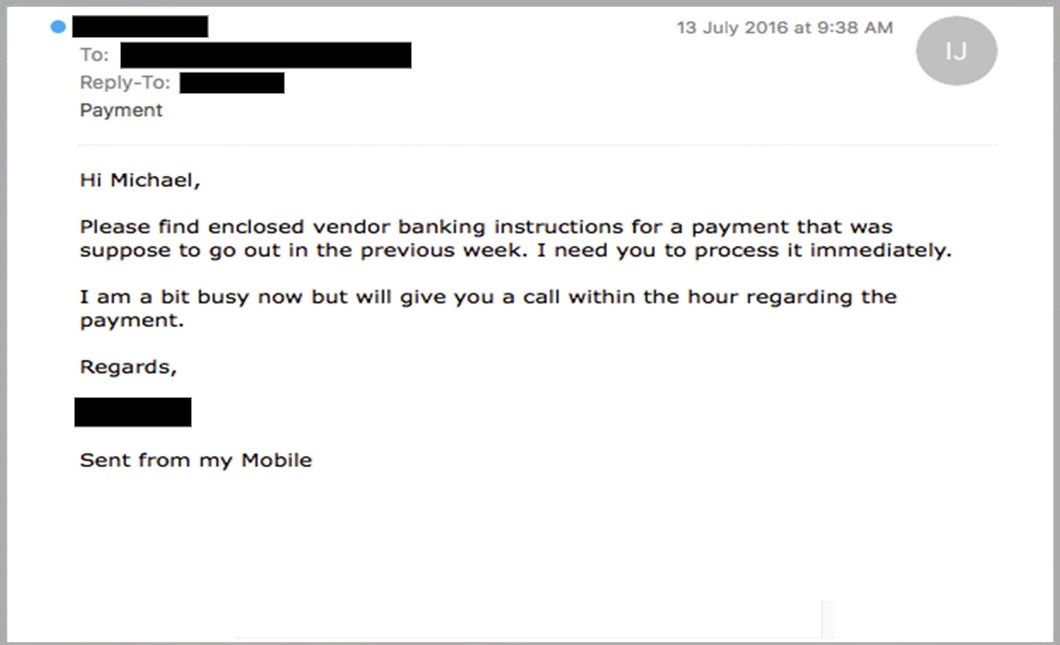
These phishing scams are especially dangerous because even if they suspect foul play, recipients might not be able to confront their boss.
They are implying that the boss requested something inappropriate if they are incorrect.
Organizations that value cyber security will accept that it’s safer to be safe than sorry, and may even commend the employee for being cautious.
Prevent phishing by educating your employees
Organizations must ensure that staff are aware of the dangers of phishing and provide ongoing training.
Your team will only be able to develop good habits and recognize malicious messages if you reinforce the advice about avoiding scams.
These lessons are easy with our Phishing Awareness Training Program.
This online course covers everything you need to know regarding phishing and is updated every month to include the most recent scams.




